How To Hack Any Wi-Fi Network Connection To Get Password Using ComView & Aircreak-Ng!
Using free internet from a password protected and any WEP WPA WPA-PSK secured WiFi network of your neighbor is not a bad idea at all! Because they won’t share passwords if you ask for it. In this case the only way is hack or creak their Wi-Fi network connection and get unauthorized access to use unlimited free internet.
Almost every hotspots are WEP secured out there. WPA & WPA-PSK are also available but only some people use this type of connection. So in this tutorial I will show you how do you can hack/creak any kind of WEP WPA WPA2 secured Wi-Fi hotspot network connection using a free Wi-Fi creaking tool that called ComView Wi-Fi program.
You can use virtual box or Linux users can read out this tutorial on How to hack Wi-Fi using Linux Backtrack.
Part 1: WEP
1. Click on File->Log Viewer->Load Commview Logs-> Choose the .ncf file.
2. Now File->Export->Wireshark/TCP dump format .
Part 2: WPA &WPA2
Just two more simple steps will be added with those previous steps shown in part one.
1. Open Aircreak-Ng GUI.
1. Select WPA insted of WEP when you are revealing password from .cap file.and put \test\password.lst in wordlist field.
Still confused? this video could help you. watch this video carefully and read my instruction carefully. success will be must!
This software works with windows xp, windows seven and may be later on. In this tutorial I am using windows 7. If you are using a different operating system, no problem.
You can use virtual box or Linux users can read out this tutorial on How to hack Wi-Fi using Linux Backtrack.
Tools to be used in this process:
ComView is a packet sniping tool. It captured packets transmitting through Wi-Fi network signal. Every packets has some information about your victims hotspot.
So, as much as your packets will be captured, the percentage of your getting password will be increased. An estimated packets limit to get all possible information is about 10000.
Normally it could take up to 2-5 hrs to complete capturing those packets depending your hotspot signal strength and speed. Captured packets will be stored in .ncp format.
So, as much as your packets will be captured, the percentage of your getting password will be increased. An estimated packets limit to get all possible information is about 10000.
Normally it could take up to 2-5 hrs to complete capturing those packets depending your hotspot signal strength and speed. Captured packets will be stored in .ncp format.
Using this program we will convert our captured .ncp packets into .cap file.
Note: please make sure you are using this computer as Administrator to install both software.
Let’s Begin To Hack:
In the first part of this tutorial I'll show you how to hack WEP and in second part WRA & WPA-PSK will be shown.
In the first part of this tutorial I'll show you how to hack WEP and in second part WRA & WPA-PSK will be shown.
Part 1: WEP
Step 1: Install ComView in VoIP or Standard mode. Remember this software will not connect you to any Wi-Fi network. It’s just a tool to gain password. Once you get hotspot password, then you know how to use it.
Step 2: Open ComViwe program and this window will appear. Click Play icon. New window will be opened.
Step 3: Click following button to start network scanning.
Step 4: Now you can see your available hotspot names. Select which one you want to hack. And click Capture button. Please be sure that your selected network is a WEP connection.
Step 5: Program has started capturing your network information.
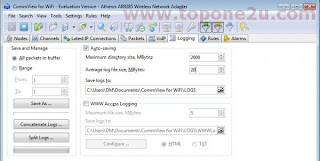
Step 6: To save the captured packets, navigate to Setting> Option>Memory Usage. Change Maximum Packets in buffer to 20000.
Step 7: Go to logging tab and enable Auto Saving. Set Maximum directory to 2000 and Log file size to 20. ComView will now automatically store captured .ncp packets to your located directory.
As comview has started auto storing, you will see a lots of captured packets are stored on the saving directory folder. You should need to compile those individual .ncp packets into a single .ncp file.
To compile: Go to CONCATENATE LOGS… Using Logging tab.
Now we will convert that .ncp file into .cap file using Aircreak-Ng.
1. Click on File->Log Viewer->Load Commview Logs-> Choose the .ncf file.
2. Now File->Export->Wireshark/TCP dump format .
Now the Final part:
Open AirCrack folder>Bin> Aircrack-ng GUI.exe. put the .cp file in GUI Location and press some next button. Done!
Now you will see the whole information about your targeted network. How much bandwidth are using this network, usernames, password, etc.
Part 2: WPA &WPA2
Just two more simple steps will be added with those previous steps shown in part one.
1. Open Aircreak-Ng GUI.
1. Select WPA insted of WEP when you are revealing password from .cap file.and put \test\password.lst in wordlist field.
Still confused? this video could help you. watch this video carefully and read my instruction carefully. success will be must!
I hope you have done it successfully. If not, don’t be late. Just put your confusion in the comment box and I’ll get back to you immediately.