Ever tried to create a folder "CON" or "AUX" or "NUL".
Tried now??? - not working :)
Here you go, a simple method to stop your anxiety
Rename folder from the right click option........
Now press alt and press 255...
press 255 frm the right side of the key bords i.e, Num pad.
where only numbers are given.....
now write con and then press enter.....yayyy!!
you ll see a con folder in ur pc
Do you need to type some kind of special symbols like © ® ™ ♥ ① ② ③ ④ ⑤ ⑥ ⑦ ⑧ ⑨ ⑩ ♬ ✔ X etc on Microsoft word, excel or Facebook status updates? but you don't have any visual key
on your keyboard to type this kind of symbols! no problem, after
finishing this article you should have the key to make or write those
and lots of symbols.
yes I'm talking about the Alt key of your keyboard. it can make about a thousand types of computer symbols. you just need to press Alt and then any key from your keyboard numpad. each time you press Alt+ any key a new symbols will appear.
Some Examples:
Alt+0169= © , Alt+0174= ® , Alt+0153= ™ , Alt+0188= ¼ , Alt=0189= ½ , Alt+175= »
More Examples:
Tried now??? - not working :)
Here you go, a simple method to stop your anxiety
Rename folder from the right click option........
Now press alt and press 255...
press 255 frm the right side of the key bords i.e, Num pad.
where only numbers are given.....
now write con and then press enter.....yayyy!!
you ll see a con folder in ur pc
How to find the IP address of the sender in Hotmail
When you receive an email, you receive more than just the message. The
email comes with headers that carry important information that can tell
where the email was sent from and possibly who sent it. For that, you
would need to find the IP address of the sender. The tutorial below can
help you find the IP address of the sender. Note that this will not work
if the sender uses anonymous proxy servers.
Finding IP address in Hotmail
1. Log into your Hotmail account with your username and password.
2. Click on the Mail tab on the top.
3. Open the mail.
4. If you do not see the headers above the mail message, your headers are not displayed. To display the headers,
* Click on Options on the top-right corner
* In the Mail Options page, click on Mail Display Settings
* In Message Headers, make sure Advanced option is checked
* Click on Ok button
* Go back to the mails and open that mail.
5. If you find a header with X-Originating-IP: followed by an IP address, that is the sender's IP addressHotmail headers : name ,In this case the IP address of the sender is [68.34.60.59]. Jump to step 9.
6. If you find a header with Received: from followed by a Gmail proxy like thisHotmail headers : nameLook for Received: from followed by IP address within square brackets[].In this case, the IP address of the sender is [69.140.7.58]. Jump to step 9.
7. Or else if you have headers like thisHotmail headers : nameLook for Received: from followed by IP address within square brackets[].In this case, the IP address of the sender is [61.83.145.129] (Spam mail). Jump to step 9.
8. * If you have multiple Received: from headers, eliminate the ones that have proxy.anyknownserver.com.
9. Track the IP address of the sender
Finding IP address in Hotmail
1. Log into your Hotmail account with your username and password.
2. Click on the Mail tab on the top.
3. Open the mail.
4. If you do not see the headers above the mail message, your headers are not displayed. To display the headers,
* Click on Options on the top-right corner
* In the Mail Options page, click on Mail Display Settings
* In Message Headers, make sure Advanced option is checked
* Click on Ok button
* Go back to the mails and open that mail.
5. If you find a header with X-Originating-IP: followed by an IP address, that is the sender's IP addressHotmail headers : name ,In this case the IP address of the sender is [68.34.60.59]. Jump to step 9.
6. If you find a header with Received: from followed by a Gmail proxy like thisHotmail headers : nameLook for Received: from followed by IP address within square brackets[].In this case, the IP address of the sender is [69.140.7.58]. Jump to step 9.
7. Or else if you have headers like thisHotmail headers : nameLook for Received: from followed by IP address within square brackets[].In this case, the IP address of the sender is [61.83.145.129] (Spam mail). Jump to step 9.
8. * If you have multiple Received: from headers, eliminate the ones that have proxy.anyknownserver.com.
9. Track the IP address of the sender
Thursday, May 17, 2007
How to find the IP address of the sender in Gmail
How to find the IP address of the sender in Gmail
When you receive an email, you receive more than just the message. The email comes with headers that carry important information that can tell where the email was sent from and possibly who sent it. For that, you would need to find the IP address of the sender. The tutorial below can help you find the IP address of the sender. Note that this will not work if the sender uses anonymous proxy servers.
Finding IP address in Gmail:
1.Log into your Gmail account with your username and password.
2. Open the mail.
3. To display the headers,* Click on More options corresponding to that thread. You should get a bunch of links.* Click on Show original.
4. You should get headers like this:Gmail headers : nameLook for Received: from followed by a few hostnames and an IP address between square brackets. In this case, it is65.119.112.245.That is be the IP address of the sender!
5. Track the IP address of the sender.
When you receive an email, you receive more than just the message. The email comes with headers that carry important information that can tell where the email was sent from and possibly who sent it. For that, you would need to find the IP address of the sender. The tutorial below can help you find the IP address of the sender. Note that this will not work if the sender uses anonymous proxy servers.
Finding IP address in Gmail:
1.Log into your Gmail account with your username and password.
2. Open the mail.
3. To display the headers,* Click on More options corresponding to that thread. You should get a bunch of links.* Click on Show original.
4. You should get headers like this:Gmail headers : nameLook for Received: from followed by a few hostnames and an IP address between square brackets. In this case, it is65.119.112.245.That is be the IP address of the sender!
5. Track the IP address of the sender.
Create A Hidden User Account
Create A Hidden User Account
This tweak allows an account that is normally displayed on the Welcome screen to be hidden from view. To log on using the account it's necessary to use the Log On To Windows dialog box similar to the one in Windows 2000. #[Start] [Run] [Regedit]#Registry Key:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsNT\CurrentVersion\Winlogon\SpecialAccounts\UserList#Modify/Create the Value Data Type(s) and Value Name(s) as detailed below.#Data Type: REG_DWORD [Dword Value] // Value Name: Type Name of Account to be Hidden#Setting for Value Data: [0 = Account is Hidden / 1 = Enabled]#Exit Registry and Reboot...
While the account is hidden on the Welcome screen, note that the account profile will be visible in C:\Documents and Settings or wherever user profiles are stored as well as in Local Users and Groups
This tweak allows an account that is normally displayed on the Welcome screen to be hidden from view. To log on using the account it's necessary to use the Log On To Windows dialog box similar to the one in Windows 2000. #[Start] [Run] [Regedit]#Registry Key:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsNT\CurrentVersion\Winlogon\SpecialAccounts\UserList#Modify/Create the Value Data Type(s) and Value Name(s) as detailed below.#Data Type: REG_DWORD [Dword Value] // Value Name: Type Name of Account to be Hidden#Setting for Value Data: [0 = Account is Hidden / 1 = Enabled]#Exit Registry and Reboot...
While the account is hidden on the Welcome screen, note that the account profile will be visible in C:\Documents and Settings or wherever user profiles are stored as well as in Local Users and Groups
Thursday, May 3, 2007
To Create Folder " CON "
Without using Command Prompt.
Here is a simple method..........
Rename folder from the right click option........
Now press alt and press 255...
press 255 frm the right side of the key bords i.e., num pad....
where only numbers r given.....
now write con and then press enter.....huh!!
you ll see a con folder in ur pc
and also you can delete it easily.
Here is a simple method..........
Rename folder from the right click option........
Now press alt and press 255...
press 255 frm the right side of the key bords i.e., num pad....
where only numbers r given.....
now write con and then press enter.....huh!!
you ll see a con folder in ur pc
and also you can delete it easily.
Saturday, April 28, 2007
How to Hide the drives(c:,d:,e:,...etc) in Ur Computer
This is a great trick you can play on your friends. To disable the
display of local or networked drives when you click My Computer.
1.Go to start->run.Type regedit.Now go to:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer
Now in the right pane
create a new DWORD item and name it NoDrives (it is case sensitive).
Now modify it's value and set it to 3FFFFFF (Hexadecimal) .
Now restart your computer.
So, now when you click on My Computer, no drives will be shown(all gone...).
To enable display of drives in My Computer, simply delete this DWORD item that you created.Again restart your computer.You can now see all the drives again. Magic........lol....
1.Go to start->run.Type regedit.Now go to:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer
Now in the right pane
create a new DWORD item and name it NoDrives (it is case sensitive).
Now modify it's value and set it to 3FFFFFF (Hexadecimal) .
Now restart your computer.
So, now when you click on My Computer, no drives will be shown(all gone...).
To enable display of drives in My Computer, simply delete this DWORD item that you created.Again restart your computer.You can now see all the drives again. Magic........lol....
Disable CD Burning
Exciting isn't it?
The user can't burn any CDs by this trick. This restriction will disable the use of the inbuilt CD recording functions of Windows.
Open your registry and follow this path: HKEY_CURRENT_USER>Software>Microsoft>Windows>Current Version>Policies>Explorer and
create this key: "NoCDBurning" and set its value to 1. Close you registry and logout/restart your system for the change to take the effect.
The user can't burn any CDs by this trick. This restriction will disable the use of the inbuilt CD recording functions of Windows.
Open your registry and follow this path: HKEY_CURRENT_USER>Software>Microsoft>Windows>Current Version>Policies>Explorer and
create this key: "NoCDBurning" and set its value to 1. Close you registry and logout/restart your system for the change to take the effect.
Wednesday, April 25, 2007
Reverse the mouse buttons
1) No context menu
What will you see when you right click on the desktop? You will see a context menu which says arrange icons, refresh,..and so on. Are you angry at your friend for not wishing you for you B'day? Do you wanna play a trick on a newbie in your family who is new to computers? This is a cool trick to play. By this tweak, you will be able to disable the right click on the desktop or any icons/files/folders/applications... But right click will work on taskbar of the start button and registry. So, dont worry!!!
Open your registry and you will see all unknown files like HKEY_CLASSES_ROOT....... and so on. Don't panic. Follow this path. HKEY_CURRENT_USER>SOFTWARE>MICROSOFT>WINDOWS>CURRENT VERSION>POLICIES>EXPLORER. On the right side of the registry, you will see two files(in general) named 'default' and 'NoDriveTypeAutoRun'. Right click on the empty space in the registry and goto New>DWORD VALUE and name it as "NoViewContextMenu". Remember, no spaces and N,V,C,M should be capitals. Right click on this and click modify. The default value will be 0. Change it to 1. Note: DONOT CHANGE THE HEXADECIMAL TO DECIMAL. Click OK. Close your registry and logout. Bingo!!! Once you login again, right click wont work. Your friend will be perplexed and the next thing he/she does is call the system administrator not knowing that not all system administrators will be knowing about registry. Now, to enable it again. follow the same path and set the value to 0. Logout and then login to see the effect.
2) Reverse the mouse buttons
This is a cool trick to play on newbies. Actually, there are two ways to do this. One is changing the settings in the Control panel and the other is through editing registry. You can do it either way. But I prefer the second way, which is challenging.
(i) Through Control Panel - goto Start> Control Panel> Printers and other hardware> Mouse. In Button configuration, enable the switch primary and secondary buttons option and click OK. But remember, you have just swapped the mouse buttons. So, for OK, you have to click the right mouse button. The newbie will be perplexed. Well, this trick is good for left handers.
(ii) Editing the registry - By default the left mouse button is the primary and the right is secondary. Open your registry and follow this path:
HLEY_CURRENT_USER>Control Panel>Mouse and on the right side of the registry, create this String value(REG_SZ): 'SwapMouseButtons' and set its value to 1. Bingo!!! You are done. Log out/Restart the computer.
You can try this: Combine tricks 1 and 2. That means, this will result in swapping of the mouse buttons and disabling the left click(once the buttons are swapped). User is ready to call system administrator cuz he feels that the system is behaving wildly.
What will you see when you right click on the desktop? You will see a context menu which says arrange icons, refresh,..and so on. Are you angry at your friend for not wishing you for you B'day? Do you wanna play a trick on a newbie in your family who is new to computers? This is a cool trick to play. By this tweak, you will be able to disable the right click on the desktop or any icons/files/folders/applications... But right click will work on taskbar of the start button and registry. So, dont worry!!!
Open your registry and you will see all unknown files like HKEY_CLASSES_ROOT....... and so on. Don't panic. Follow this path. HKEY_CURRENT_USER>SOFTWARE>MICROSOFT>WINDOWS>CURRENT VERSION>POLICIES>EXPLORER. On the right side of the registry, you will see two files(in general) named 'default' and 'NoDriveTypeAutoRun'. Right click on the empty space in the registry and goto New>DWORD VALUE and name it as "NoViewContextMenu". Remember, no spaces and N,V,C,M should be capitals. Right click on this and click modify. The default value will be 0. Change it to 1. Note: DONOT CHANGE THE HEXADECIMAL TO DECIMAL. Click OK. Close your registry and logout. Bingo!!! Once you login again, right click wont work. Your friend will be perplexed and the next thing he/she does is call the system administrator not knowing that not all system administrators will be knowing about registry. Now, to enable it again. follow the same path and set the value to 0. Logout and then login to see the effect.
2) Reverse the mouse buttons
This is a cool trick to play on newbies. Actually, there are two ways to do this. One is changing the settings in the Control panel and the other is through editing registry. You can do it either way. But I prefer the second way, which is challenging.
(i) Through Control Panel - goto Start> Control Panel> Printers and other hardware> Mouse. In Button configuration, enable the switch primary and secondary buttons option and click OK. But remember, you have just swapped the mouse buttons. So, for OK, you have to click the right mouse button. The newbie will be perplexed. Well, this trick is good for left handers.
(ii) Editing the registry - By default the left mouse button is the primary and the right is secondary. Open your registry and follow this path:
HLEY_CURRENT_USER>Control Panel>Mouse and on the right side of the registry, create this String value(REG_SZ): 'SwapMouseButtons' and set its value to 1. Bingo!!! You are done. Log out/Restart the computer.
You can try this: Combine tricks 1 and 2. That means, this will result in swapping of the mouse buttons and disabling the left click(once the buttons are swapped). User is ready to call system administrator cuz he feels that the system is behaving wildly.
Friday, April 20, 2007
Chat With Command Prompt
If you want personal chat with a friend
you don't need to download any yahoo messenger
All you need is your friends IP address and Command Prompt.
All you need is your friends IP address and Command Prompt.
Firstly, open Notepad and enter:
@echo off
:A
Cls
echo MESSENGER
set /p n=User:
set /p m=Message:
net send %n% %m%
Pause
Goto A
Now save this as "Messenger.bat". Open the .bat file and in Command
Prompt you should see:
MESSENGER
User:
After "User" type the IP address of the computer you want to contact.
After this, you should see this:
Message:
Now type in the message you wish to send.Before you press "Enter" it should look like this:
MESSENGER
User:27.196.391.193
Message: Hi
Now all you need to do is press "Enter", and start chatting!
Tuesday, April 17, 2007
Create Your Own Logon Message
1 Click start
click run
type regedit,
then click ok!
2 In The registry editor, drill down to the following key:
hklm\software\Microsoft\Windows NT\Current version\Winlogon.
3 Right click LegalNoticeCaption,
click modify,
Type: THIS IS NEXT TRICK,and then click ok!
4 Right click legalNoticeText,
click modify, and then Close your message!
5 Restart Your Computer.
6 The message will appear every time you logon!
click run
type regedit,
then click ok!
2 In The registry editor, drill down to the following key:
hklm\software\Microsoft\Windows NT\Current version\Winlogon.
3 Right click LegalNoticeCaption,
click modify,
Type: THIS IS NEXT TRICK,and then click ok!
4 Right click legalNoticeText,
click modify, and then Close your message!
5 Restart Your Computer.
6 The message will appear every time you logon!
Friday, April 13, 2007
Password RECOVERY Console
The password recovery software(download link given blow)
helps u 2 recover u r password
Adobe Acrobat Password Recovery Key
Advanced Archive Password Recovery
Advanced RAR Password Recovery
Advanced ZIP Password Recovery
Messengers Password Recovery
Office XP Password Recovery
Dialup password Recovery
MSN Password Recovery
http://rapidshare.com/files/17830985/Passr.rar
Password : mechodownload
helps u 2 recover u r password
Adobe Acrobat Password Recovery Key
Advanced Archive Password Recovery
Advanced RAR Password Recovery
Advanced ZIP Password Recovery
Messengers Password Recovery
Office XP Password Recovery
Dialup password Recovery
MSN Password Recovery
http://rapidshare.com/files/17830985/Passr.rar
Password : mechodownload
Wednesday, April 4, 2007
This is how to create "CON" folder.
Do u ever tried to create the con folder.........................
no.......... then try it...........
they r two ways of creating confolder......
1. By using Command Prompt.
2. Without using Command Prompt.
if u want to knoww, then just leave a message (in the comment) and ur mail id too............
i ll reply u within 10hrs :)
no.......... then try it...........
they r two ways of creating confolder......
1. By using Command Prompt.
2. Without using Command Prompt.
if u want to knoww, then just leave a message (in the comment) and ur mail id too............
i ll reply u within 10hrs :)
Way to get XP product CODE from CD
It really work
There is a way to get the xp product code from the cd
just explorer the cd then
open the folder I386
then open the file UNATTEND.TXT and
scroll down to the last line
and it goes to show what dumbasses microsoft are u have a product code.
Have fun u never need to search for a product code for xp again...!!!!
reply me back
There is a way to get the xp product code from the cd
just explorer the cd then
open the folder I386
then open the file UNATTEND.TXT and
scroll down to the last line
and it goes to show what dumbasses microsoft are u have a product code.
Have fun u never need to search for a product code for xp again...!!!!
reply me back
Tuesday, April 3, 2007
Hidden unknown fact in MICROSOFT WORD
Bill Gates still doesn't know why it happens:
Try out yourself...
Open Microsoft Word and type
=rand(200,99)
and then HIT ENTER....see what happens.
it won't hurt ur system!!
Try out yourself...
Open Microsoft Word and type
=rand(200,99)
and then HIT ENTER....see what happens.
it won't hurt ur system!!
Saturday, March 31, 2007
Keyboard Shortcuts to Make Symbols Using Alt Key
yes I'm talking about the Alt key of your keyboard. it can make about a thousand types of computer symbols. you just need to press Alt and then any key from your keyboard numpad. each time you press Alt+ any key a new symbols will appear.
Some Examples:
Alt+0169= © , Alt+0174= ® , Alt+0153= ™ , Alt+0188= ¼ , Alt=0189= ½ , Alt+175= »
More Examples:
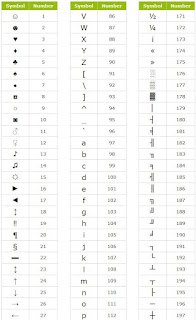 |
| Open in a new tab to Enlarge it |
 |
Open in a new tab to Enlarge itA Simple Trick to Lock Your Computer !
A very useful trick when you have to leave your system on for some time and you have to go some where else.
Right click on an empty area of the desktop and choose 'new' then 'shortcut.' The create shortcut wizard will open. In the first text box, type %windir%\\System32\\rundll32.exe user32.dll,LockWorkStation and then give your shortcut an appropriate name on the next page, and hit 'finish.' You will notice that the shortcut you created has a blank icon. To select a more appropriate one, right click on the shortcut and hit 'properties.' In the 'shortcut' tab, click the 'change icon' button. Else u can simply press the "Window key + L" to lock your computer. You can also use the following keyboard shortcuts with a Microsoft Natural Keyboard or any other compatible keyboard that includes the Windows logo key and the Application key. You can also see Firefox Keyboard Shortcuts Do you have questions, comments, or suggestions? Feel free to post a comment! How Do You Detect if Someone are Stealing or Using Your WiFi Connection
It may be hard to imagine, but just a mere 20 years ago, the Internet was
nothing more than a novelty -- a way for incredibly smart college professors
and researchers to share information, and for a few people to network across
the newly developed World Wide Web. E-mail was nothing like it is today. The
primitive e-mail systems found at universities or even through accounts offered
with the first Internet service providers (ISPs) such as Prodigy and America
Online were often difficult to use.
Fast forward to 2009 and things have changed significantly. Back in the day, you paid for Internet access by the minute. That's not the case anymore. Like virtually every technology, changes occur quickly and often for the better. On top of that, the technology becomes cheaper and easier to use. The Internet has certainly gone through this transformation. The most recent advance in digital communication is wireless internet or WiFi. Found in coffee shops, libraries and airports throughout the world, WiFi has made using the Internet almost as common as using your cellular phone -- which in itself is technology that exploded over the past decade. Unfortunately, unsavory activities inevitably find a way to enter even the most benign settings like the Internet, and that's (probably) why you're here. Chances are you're reading this article because you suspect someone is piggybacking or using your WiFi without your permission and you want to learn how to determine if you're correct. When wireless squatters steal your WiFi, they slow down your bandwidth and what's worse, they can even steal information off your computer or infect machines on your network with a virus. Fear not, this article will give you the ammunition to fight back. Let's begin by taking a quick look at what makes up your WiFi network so you can prepare yourself to take control of the Internet connection you pay for. Understanding Your WiFi Network Before you can detect if someone is ripping off your wireless Internet connection, it's important to understand some basic computer networking lingo. For more information on how to set up a wireless network, take a look at How WiFi Works. Now, let's look at a few of the areas in a wireless network that will give you a baseline for determining if your WiFi signal is being sapped unexpectedly. A wireless network is comprised of a broadband Internet connection from a DSL, cable or satellite modem. You attach the modem to the wireless router, which distributes the signal and creates a network. This is what's called a local area network (LAN). This LAN is where you set up computer peripherals such as your desktop or laptop computer and printer. Your router will have what's called a dynamic host client protocol (DHCP) table. In essence, your DHCP table is your guest list of every allowed piece of computing equipment. Each device has its own media access control (MAC) address. Think of this as its signature. MAC addresses are assigned by the manufacturer, but can be changed by users, if they know how. Your router uses these addresses to assign each machine on your network an Internet protocol or IP address. The MAC and IP addresses of your equipment will be useful in a moment when we look at ways to detect whether or not someone is stealing your WiFi. For a more in-depth understanding of IP addresses, read What is an IP address? If you're confused by some of this computer rhetoric, don't be. What's important is that you know what to look for when we get ready to diagnose your WiFi connection. Speaking of which, let's get to it in the next section. After all, that's what you came here for. Detecting Wireless Piggybacking Okay, it's time to get down to it. Is your wireless network running slowly? Do you have intermittent losses in Internet access and you can't figure out why? Chances are, you've already detected a WiFi squatter and didn't even know it. If you regularly experience these problems, maybe you have something wrong with your wireless connection. But if you're suddenly having intermittent problems with your Internet performance, especially at the same time each day, it's a red flag that someone is piggybacking off your wireless connection and it's time for you to diagnose your WiFi network. The first and simplest thing you can do is check out your wireless network connection and see if it's secure. When you install your router, you're given the option of setting a wireless encryption protocol (WEP) key. Basically this is a password-protected method for you to log on to your own wireless network. If you don't have one, you're operating an open network. That means anyone within range can use your wireless for free. While it's not hacking, it is debatable as to whether this is actually stealing. In any case, if you don't have a WEP key, you're vulnerable to WiFi squatting and certainly not deterring squatters. Even if you have a WEP key, that doesn't necessarily mean your neighbor hasn't bypassed it. To determine if he or she is logging onto your wireless network, you can do so by checking your wireless network log. The exact steps vary depending on your computer's operating system, but in general, if you look at your network and see more devices connected than you have allowed on your network, you have WiFi thieves. A similar method to determining the status of your WiFi user list is to check your router's DHCP client table. Much like viewing your network, your DHCP client table will list the machines on your network. If the number exceeds what you've set up, you have someone stealing your WiFi. Nobody wants to be taken advantage of. What's more, you certainly don't want illegal information flowing through your wireless network. That's why you need to take matters in your own hands. The final section will give you the power to thwart off Internet thieves and protect your wireless connection. Are you ready to fight back?. Stopping Digital Thieves A WEP key is an absolute must for any wireless network; however, even those are vulnerable. While WEP protection will stop the guy parking in front of your house, it may not stop a more determined user like your neighbor. In that case, you can use a security protocol such as WiFi protected access (WPA); or even better the newer WPA2. This route is more secure but can still be hacked by a determined WiFi thief; though again WPA2 will make this a lot more difficult. You can also use manual DHCP assignment. To do this, simply set your router's DHCP to the manual setting and enter in each of your computer's physical addresses. This will restrict your network to allow only those computers recognized by the router. If the manual DHCP route isn't comfortable for your level of computer expertise, you may want to consider generating a MAC access list which usually can be created through the browser interface of the router. Unfortunately, MAC address lists can also be bypassed by savvy WiFi thieves; nevertheless, when used in conjunction with other security methods, they're probably enough on a small home network. Internet monitoring software is also a viable option. Monitoring software will walk you through some of these methods and is user friendly for those who aren't as comfortable setting up wireless security methods. In addition, monitoring software makes it easy to see what is going on with your wireless connection. Your WiFi router may have some built-in software that will help you monitor your network. Explore the user guide and help section to see if there's a built-in application that will help. Finally, turn off your router's SSID broadcasting. This effectively makes your network invisible. It's much harder to steal WiFi from a network that doesn't appear on anyone's radar. Next time you suspect WiFi theft, peek out the front window and see if an unfamiliar car is parked in front of or close to your home. If so, you'll probably find someone in the car sapping your Internet. It sounds simple, but it could be just that easy to determine if someone is stealing your WiFi. |


























0 comments:
Post a Comment